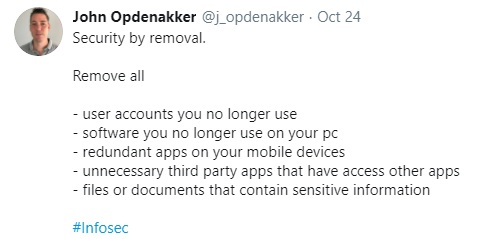
Inspired by the succinct Tweet below, KnowIT recommends operating your company from a "security by removal" framework, if you are looking to start securing your IT on your own.
What we love most about this tip is how succinct it puts it for business owners to follow!
Whether you’re looking to sit down on a call with your IT team to discuss what you no longer are using day-to-day or if you’re looking to self-audit, this is a great starting point.
Unnecessary user accounts serve as potential attack vectors for those looking to infiltrate your system. Disabling accounts as soon as staff leave the company is an important step; removing superfluous accounts on your network periodically is as well.
If you check “add or remove programs” on your computer, how many do you notice that you’re no longer using for business? Many systems hold out-of-date software that is not being used (or updated!) and serves as a vulnerable spot in your network.
Check your phones and tablets! If you have your apps organized into folders, like many of us do, it’s too easy to have folders that we stop entering regularly. While it might be handy to have those apps accessible at anytime, if you find yourself going a month without using it, consider whether or not it needs to live on your device.
Think twice about how you are retaining sensitive information on a long-term basis. Microsoft offers sensitivity labeling that can help you identify and secure what needs to be kept. Set up reminders annually, quarterly, or monthly to review and purge any information that does not need to be kept.
Checklist for Removal:
User Accounts No Longer In Use
Software No Longer Used on Computer(s)
Redundant and Unused Apps on Mobile Devices
Files, Documents, and Emails Containing Sensitive Information